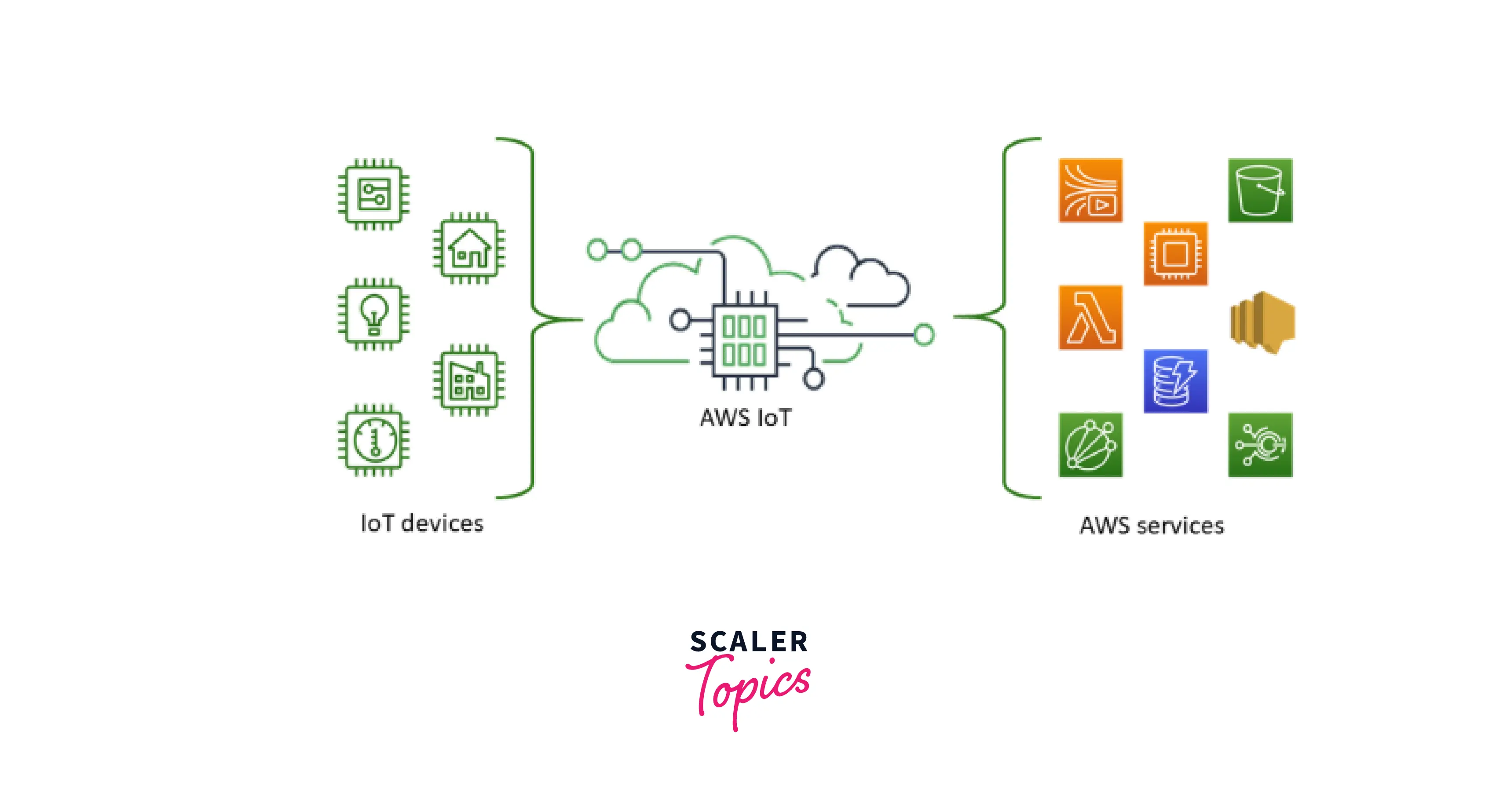
When it comes to managing IoT devices in the cloud, AWS IoT Core SSH provides a seamless and secure way to connect, monitor, and manage your devices remotely. With AWS IoT Core, businesses can harness the power of the Internet of Things (IoT) to streamline operations, enhance productivity, and drive innovation. However, ensuring secure communication between your devices and AWS IoT Core is critical to maintaining data integrity and protecting sensitive information. This is where SSH (Secure Shell) comes into play, offering a robust protocol for secure access and management.
AWS IoT Core SSH is not just about connectivity; it’s about enabling secure, scalable, and efficient communication between your IoT devices and the AWS ecosystem. Whether you’re a developer, an IoT engineer, or a business owner, understanding how to leverage AWS IoT Core with SSH can significantly enhance your IoT infrastructure. From remote device management to secure data transfer, AWS IoT Core SSH provides the tools you need to succeed in the IoT landscape.
In this guide, we’ll explore the ins and outs of AWS IoT Core SSH, from setting up secure connections to troubleshooting common issues. We’ll also address key questions like “How does AWS IoT Core SSH work?” and “What are the best practices for securing IoT devices?” By the end of this article, you’ll have a comprehensive understanding of how to use AWS IoT Core SSH to optimize your IoT operations while ensuring the highest level of security.
Read also:How To Download Web Series Safely And Legally A Complete Guide
Table of Contents
- What is IoT Core SSH AWS?
- How Does AWS IoT Core SSH Work?
- Why is Secure Connectivity Important in IoT Core SSH AWS?
- How to Set Up SSH for AWS IoT Core?
- Common Challenges in IoT Core SSH AWS
- Best Practices for Securing IoT Devices with SSH
- What Are the Benefits of Using IoT Core SSH AWS?
- How to Troubleshoot Issues in IoT Core SSH AWS?
- Real-World Applications of IoT Core SSH AWS
- Future Trends in IoT Core SSH AWS
What is IoT Core SSH AWS?
AWS IoT Core SSH is a secure protocol that allows users to connect to IoT devices managed through AWS IoT Core. AWS IoT Core is a managed cloud service that lets connected devices interact with cloud applications and other devices securely. By integrating SSH into this framework, users can remotely manage their IoT devices, execute commands, and transfer data securely. This combination of AWS IoT Core and SSH ensures that your IoT infrastructure is both scalable and secure.
The integration of SSH with AWS IoT Core provides an additional layer of security by encrypting data during transmission. This is particularly important for businesses that rely on IoT devices to collect and transmit sensitive data. With AWS IoT Core SSH, you can ensure that your devices are protected from unauthorized access and potential cyber threats.
How Does AWS IoT Core SSH Work?
AWS IoT Core SSH works by establishing a secure connection between your IoT devices and the AWS cloud. When you initiate an SSH session, the protocol encrypts all data transmitted between the device and the server. This ensures that even if the data is intercepted, it cannot be read or tampered with by unauthorized parties.
To use AWS IoT Core SSH, you need to configure your IoT devices to support SSH and ensure that they are registered with AWS IoT Core. Once configured, you can use SSH to remotely access your devices, execute commands, and manage configurations. This makes it easier to maintain and troubleshoot your IoT infrastructure without needing physical access to the devices.
Why is Secure Connectivity Important in IoT Core SSH AWS?
Secure connectivity is crucial in IoT Core SSH AWS because IoT devices often handle sensitive data, such as personal information, financial data, or operational insights. Without secure connectivity, this data could be vulnerable to cyberattacks, leading to potential data breaches and financial losses.
By using AWS IoT Core SSH, businesses can ensure that their IoT devices are protected from unauthorized access and data breaches. The encryption provided by SSH ensures that all data transmitted between devices and the cloud is secure, reducing the risk of interception or tampering.
Read also:Discover The Best Of Entertainment With Yo Moviescom 2024
How to Set Up SSH for AWS IoT Core?
Setting up SSH for AWS IoT Core involves several steps, including configuring your IoT devices, generating SSH keys, and registering your devices with AWS IoT Core. Here’s a step-by-step guide to help you get started:
- Configure Your IoT Devices: Ensure that your IoT devices support SSH and are properly configured to accept SSH connections.
- Generate SSH Keys: Use an SSH key generator to create a public and private key pair. The public key will be uploaded to AWS IoT Core, while the private key will remain on your local machine.
- Register Devices with AWS IoT Core: Register your IoT devices with AWS IoT Core and associate them with the public SSH key.
- Test the Connection: Once everything is set up, test the SSH connection to ensure that it is working correctly.
Common Challenges in IoT Core SSH AWS
While AWS IoT Core SSH offers many benefits, there are also some challenges that users may encounter. These include:
- Device Compatibility: Not all IoT devices support SSH, which can make it difficult to implement in some cases.
- Key Management: Managing SSH keys across multiple devices can be complex, especially for large-scale IoT deployments.
- Network Issues: Connectivity problems can disrupt SSH sessions, making it difficult to manage devices remotely.
Best Practices for Securing IoT Devices with SSH
To ensure the security of your IoT devices when using AWS IoT Core SSH, follow these best practices:
- Use Strong Passwords: Always use strong, unique passwords for your SSH connections.
- Limit Access: Restrict SSH access to only those users who need it.
- Regularly Update Software: Keep your IoT devices and SSH software up to date to protect against vulnerabilities.
What Are the Benefits of Using IoT Core SSH AWS?
Using AWS IoT Core SSH offers several benefits, including:
- Secure Communication: SSH encrypts data during transmission, ensuring secure communication between devices and the cloud.
- Remote Management: With SSH, you can remotely manage your IoT devices, making it easier to maintain and troubleshoot your infrastructure.
- Scalability: AWS IoT Core SSH is designed to scale with your IoT deployment, making it suitable for both small and large-scale operations.
How to Troubleshoot Issues in IoT Core SSH AWS?
If you encounter issues with AWS IoT Core SSH, consider the following troubleshooting steps:
- Check Network Connectivity: Ensure that your devices have a stable internet connection.
- Verify SSH Configuration: Double-check your SSH settings to ensure they are correct.
- Review Logs: Check the logs for any error messages that can help identify the issue.
Real-World Applications of IoT Core SSH AWS
AWS IoT Core SSH is used in various industries to manage IoT devices securely. Some real-world applications include:
- Healthcare: Securely managing medical devices and patient data.
- Manufacturing: Monitoring and controlling industrial equipment remotely.
- Smart Homes: Managing smart home devices and ensuring secure communication.
Future Trends in IoT Core SSH AWS
As IoT continues to grow, so will the need for secure connectivity solutions like AWS IoT Core SSH. Future trends in this space include:
- Increased Adoption: More businesses will adopt AWS IoT Core SSH to secure their IoT deployments.
- Enhanced Security Features: AWS will likely introduce new security features to further enhance SSH capabilities.
- Integration with AI: AI-driven tools may be integrated with AWS IoT Core SSH to automate device management and improve security.
In conclusion, AWS IoT Core SSH is a powerful tool for managing IoT devices securely. By understanding how it works and following best practices, you can ensure that your IoT infrastructure is both scalable and secure. Whether you’re new to IoT or an experienced professional, mastering AWS IoT Core SSH is essential for success in the IoT landscape.